Access Controls: Safeguarding Your Digital Perimeter
Access Controls: Safeguarding Your Digital Perimeter

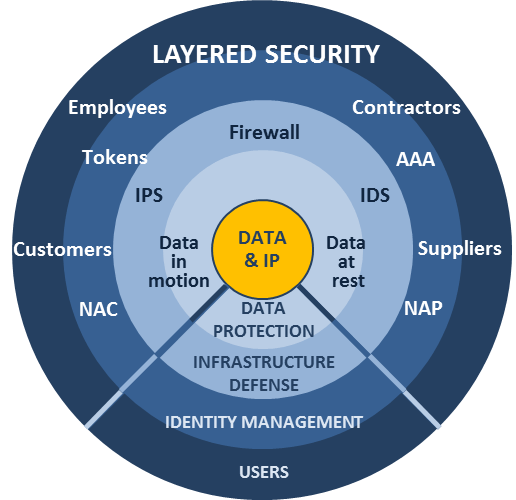
SemperSys specializes in implementing robust access controls to fortify your organization's digital perimeter. If you're visiting our website, you're likely seeking ways to enhance security by controlling and managing user access to critical systems and data. Our dedicated team collaborates closely with clients like you to design, implement, and manage effective access control solutions that safeguard your organization against unauthorized access and potential security threats.
Access controls are a fundamental aspect of cybersecurity, governing who can access what within your organization's digital ecosystem. At SemperSys, we understand the paramount importance of access controls in protecting sensitive data, maintaining compliance, and ensuring a secure operating environment.
Needs Assessment & Role Definition
We conduct a comprehensive assessment of your organization's needs, defining specific roles and responsibilities to establish the foundation for access control.
Access Control Policies & Procedures
We develop and implement access control policies and procedures, outlining the rules and guidelines for granting and revoking access rights.
User Authentication & Authorization
We establish secure authentication mechanisms and authorization processes, ensuring that only authorized users can access specific systems and data.
Role-Based Access Control (RBAC)
We implement RBAC models, assigning permissions based on job roles, responsibilities, and functions, streamlining access management and reducing risks.
Access Monitoring & Auditing
We integrate monitoring and auditing tools to track user activities, ensuring compliance, detecting suspicious behavior, and swiftly addressing potential security incidents.
Multifactor Authentication (MFA)
We advocate for MFA, adding an extra layer of security by requiring users to provide multiple forms of verification before granting access.
Privileged Access Management (PAM)
We implement PAM solutions to secure and monitor privileged accounts, minimizing the risk associated with high-level access.
Employee Training & Awareness
We conduct training sessions to educate your staff on access control best practices, promoting a security-conscious culture within your organization.
From Our Minds to Yours
 Future Work
IT tool
AI technology
Artificial Intelligence
Automation
Augmented Analytics
RPA Bots
Chatbots
Cybersecurity
Predictive Maintenance
Innovation
Data Science
Digital Transformation
Future Work
IT tool
AI technology
Artificial Intelligence
Automation
Augmented Analytics
RPA Bots
Chatbots
Cybersecurity
Predictive Maintenance
Innovation
Data Science
Digital Transformation
We immerse our expertise in your unique objectives to foster boundless acceleration as we dive into the DNA of your industry.
We Commit to Constant Improvement